On active directory auditing we want to know who, when and where the Active Directory Attributes are changed, like who removed the group from an Active directory user account, who changed the account description or any other Active directory object attribute changes
All Active directory object changes are stored in object Meta and can be viewed through repadmin command, it’s been very useful if you want to know the last changes on any attributes in an object (User Object, Computer Object, Group Object and any other AD Object)
To get the LDAP path/ User DN
Dsquery user –name <name>
To get LDAP path for Group, Computer, OU and other object, please check Find distinguished name (LDAP path for the object)
To List the User object Meta
Repadmin /showobjmeta <User DN>
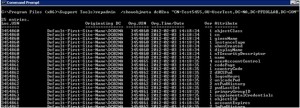
On the above Repadmin /showobjmeta output, list all the attribute changes with attribute name on the right side and when the change happened with time and date on Org.Time/Date, we also get the Originating DC
- From output, find the attribute name and check the Originating Domain Controller for that attribute change
- Log in to Originating Domain Controller
- Open the Event viewer
- Select the Security logs
- Scroll down to date and time on the Org.Time/Date
- Now you will see attribute change Event with who done the change
Event log might get overwritten and you won’t able to see the logs for requited date and meta will only show the last attribute change even it got attribute updated many times, if user membership removed on Monday and Friday, we only able to find the Fridays change because the user Meta on Active Directory been overwritten on Friday, you can use this to do active directory auditing



Thanks for sharing this informative article.
I also find a well described PDF guide that covers the same concern in order to track every critical changes occurred into Active Directory at granular level and get instant notification alerts into real time