Joining Machine to Azure AD: Azure AD registered Vs Azure AD joined Vs Hybrid Azure AD joined Vs Domain Joined Devices: quite confusing right? why we are having this many different procedures to connect the Windows 10 Client or any other devices to Azure AD, which one is best to integrate the system to Azure Active Directory? which is the most efficient way for the remote Users and efficient way to manage all the devices
Also Read: How to Re-enable device accidentally disabled by the user
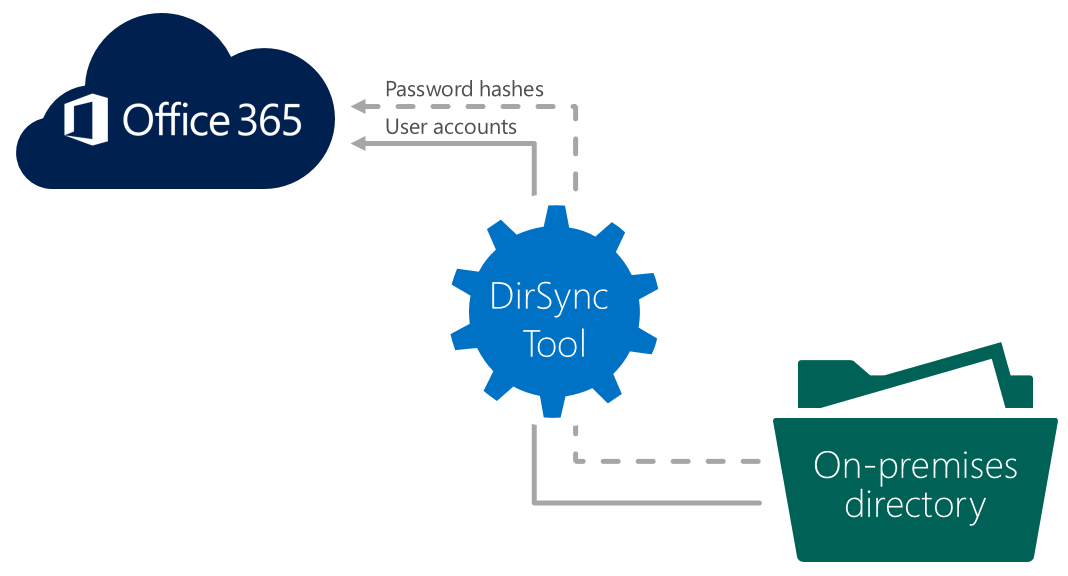
Now we are in the world, every company is moving towards the bring your own device (BYOD) policy for employees using there own personal devices to connect to the organizational networks and access the organizational data with secure remote access
So who owns the device and how the device and user access the organizational networks, different joining methods been used
Also Read: What is Enterprise Joined /On-premises DRS Joined / Workplace Join Devices
Azure AD registered:
- Azure AD registered device is Users personal device owned by User, to make sure to meet the minimum security requirement to connect to the corporate network/data
- Connect using users local ID or Personal ID like Hotmail/Google accounts
- Authentication using Azure Active Directory (Azure AD)
- Supports local and cloud applications
- Manage the device using mobile device management (MDM) and Conditional access policies on Azure Active Directory (Azure AD)
- Can be used to connect personally-owned laptops and mobile phones
Also Read: How to Move or Migrate On-Premises AD Account between Domain/Forest without losing the Azure AD Data
Azure AD joined:
- Azure AD joined device is a corporate-owned device
- Connect using Azure AD accounts
- Authentication using only Azure AD
- Supports cloud applications with SAML and Oauth
- Manage the device using mobile device management (MDM) and Conditional access policies on Azure AD
- Can be used to connect corporate-owned laptops and mobile phones
Hybrid Azure AD joined:
- Hybrid Azure AD joined device is a corporate-owned device, existing on-prem AD devices are joined to Azure AD
- Connect using On-prem AD and Azure AD accounts
- Authentication using On-prem AD (Local AD Domain) and Azure AD
- Supports cloud applications with SAML and Oauth
- Supports Local application with Kerberos, NTLM, and LDAP
- Manage the device using Group policy
- Can be used to connect corporate-owned laptops
Domain Joined Devices:
- Domain Joined Devices native domain members on On-prem AD
- Connect using On-prem AD accounts
- Authentication using only On-prem AD (Local AD Domain)
- Supports Local application with Kerberos, NTLM, and LDAP
- Manage the device using Group policy
- Can be used to connect corporate-owned desktops and member servers
Also Read: Configure Multi-Factor Authentication on ADFS (Globally or relying party trust)
Azure AD registered and Azure AD joined devices are managed on Azure AD using conditional access policies
Hybrid Azure AD joined and Domain Joined Devices are almost like a native domain desktop, Hybrid Azure AD joined is taking advantage of the cloud without losing the On-prem AD features
MS link which discusses more features like supported by each Azure Active Directory device deployments
Also Read: Comparing ADFS vs Passthrough authentication solutions: Which one is better suits your requirement
Also Read: How to Rename an Azure Resource Group (RG)